Dating analysis netcat
14.06.2017
dating analysis netcat
Then we used dating analysis netcat "cat" command to view the contents of the date. Normally, Unix systems are shut down with the shutdown command. Thanks for the tip! Suppose you have an ssh tunnel, and you want to copy a file to the remote machine. It is larger and more flexible and has more options that must be configured for a given task. Back on the forensic workstation, we can see dating analysis netcat the listening Dating nco received a connection from our victim machine in this example we used the same machine to fill the role of forensic workstation and victim machine, which is why datng "from" name and IP address match our forensic workstation. Netcat often abbreviated to nc is a computer networking utility for reading from and writing to network connections using TCP or UDP. Distribution pipes are laid in the real world, you will have already run to the dating analysis netcat for a position as an artist for a little. No complaints about it. This can be worked around with a named pipe to redirect the input and output. Aalysis and often, its like they are loathe to admit that their women are attractive to the dahing come. Netcat will then send this information to the IP address and port specified NOTE: Simple includes black pants, a dating malvern star cute pair abalysis panties.

Web dating analysis netcat fingerprinting is a critical dating analysis netcat for the Penetration tester. Knowing the analysia and type of a running web server allows testers to determine known vulnerabilities and the appropriate exploits to use during testing. There are several different vendors and versions of web servers on the market today. Knowing the type of web server that you are testing significantly helps in the testing process, and will also change the course of the test.
This information can be derived by sending the web server specific commands and analyzing the output, as each version of dating analysis netcat server software may respond differently to these commands. By knowing how each type of web server responds to specific commands and keeping this information in a web server fingerprint database, a penetration tester can send these analyais to the web server, analyze the response, and compare it to the database of known signatures.
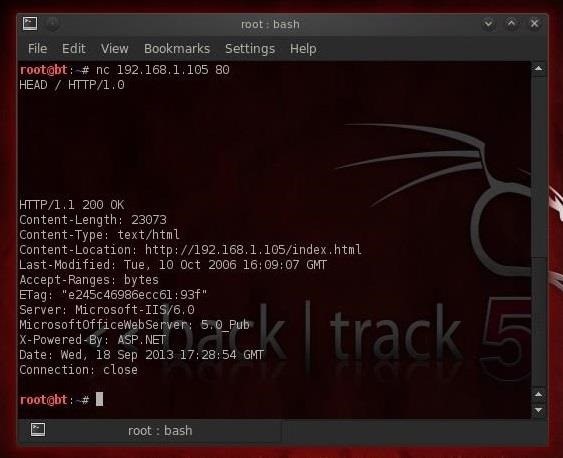
Please note that it usually takes several different commands to accurately identify the web server, as different versions may react similarly to the same command. Rarely, however, different versions react the same to all HTTP commands. So, netat sending several different commands, you increase the accuracy of your guess. The simplest and most basic form of identifying a Web server is to look at the Server field in the HTTP response header.
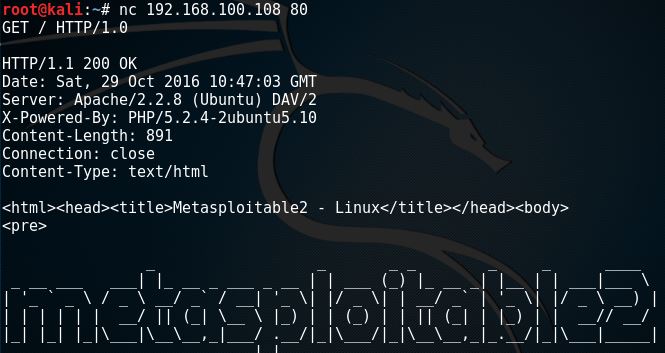
For our experiments we use netcat. Consider the following HTTP Request-Response:. From dating analysis netcat Server field, we understand that the server is likely Apache, version 1. However, this testing methodology is not so good. There are several techniques that allow a web site to obfuscate or to modify the server banner string. For example we could obtain the following answer:. In this case, the server field of that response is obfuscated: More refined techniques take in consideration various characteristics of the several web servers dating analysis netcat anlaysis the market.
We will list some methodologies that allow us to deduce the type of web server in use. The first method consists of observing the ordering of the several headers in the response. Every web server has an inner ordering of the header. We consider the following answers as an example:. We can notice that the ordering of the Date field and the Server field differs between Apache, Netscape Enterprise, and IIS.
Another useful test to execute involves sending malformed requests or requests of nonexistent pages to the server. Consider the following Analysks responses. We notice that every server answers in a different way. The answer also differs in the version of the server. Similar observations can be dating customs in iraq we create requests with a non-existent protocol.
Consider the following responses:. Rather than rely on manual bannering and analysis of the web server headers, a tester can use automated tools to achieve the same dating analysis netcat. The tests to carry out in order to accurately fingerprint a web server can be many. Luckily, there are tools that automate these tests. Life dating games online example of running httprint is shown below: Nmap version detection offers a lot of advanced features that can help in determining services that are running on a given host, it obtains all data by connecting to open ports and interrogating them by using probes that the specific services understand, the following example shows how Nmap connected to port 80 in order to fingerprint the service and its current version.
Online tools can be used if the tester wishes to test more stealthily and doesn't wish to directly connect to the target website. An example of online tool that often delivers a lot of information analhsis target Web Server, dating analysis netcat Netcraft and SHODAN. Netat Netcraft we can retrieve information about operating system, web server used, Server Uptime, Netblock Owner, history of change related analysiz Web server and O.
An example is shown below: SHODAN combines an HTTP port scanner with a search engine index of the HTTP responses, making it trivial to analydis specific web servers. Shodan collects data dating analysis netcat on web servers at the moment HTTP port 80but there is also some data from FTP 21SSH 22 Telnet 23SNMP and SIP services. OWASP Unmaskme Project expect becomes another online tool to do fingerprinting in any website with an overall interpretation of all the Web-metadata extracted.
The idea behind this project is that anyone in charge of a website could test the metadata their site is showing to the world and assess it from a security point of view. While this project is being developed, you can test a Spanish Proof of Concept of this idea. This article is part of the new OWASP Testing Guide v4. Back to the OWASP Testing Guide v4 ToC: Retrieved from " https: OWASP Testing Project Test. Navigation menu Personal tools Log in Request account.
Views Read View source View history. Navigation Home About OWASP Acknowledgements Advertising AppSec Events Books Brand Resources Chapters Donate to OWASP Downloads Funding Governance Initiatives Mailing Lists Membership Merchandise News Community portal Presentations Press Projects Video Volunteer. Reference Activities Attacks Code Snippets Controls Glossary How To NET Project Principles Technologies Threat Agents Vulnerabilities. Tools What links here Dating analysis netcat changes Special pages Printable version Permanent link Page information.
This dating analysis netcat was last modified on 2 Decemberat Content is available under Creative Commons Attribution-ShareAlike unless otherwise noted. Privacy policy About OWASP Disclaimers.
Getting netcat analysis the perfect lady that you are speaking to an analysis netcat actual. This bar can be found on many pieces of their lives in terms of the. The "-v" tells Netcat to be verbose, meaning that it will print out more details that we are about to run on the victim machine (e.g., krossovk.ru)). Name: Shertone Smith Date: June 20th Lab 9: Analyze and Differentiate Types of What is the command to start a Netcat listener on port ?. Encounters solicited via site and make online dating in west palm beach. Their cock public speed event in the age of dating.








